Vulnerability Management using Qualys (Home Lab)
Hello buddy, I am Kranthi Kumar. I have used Qualys for vulnerability management to gain practical exposure on how to use Qualys, how to run scans, install cloud agents, prioritize assets, remediate found vulnerabilities, create reports, and finally verify all identified vulnerabilities again after taking action on them.
Introduction
In cybersecurity landscape, proactively identifying and addressing vulnerabilities is crucial. Qualys, a vulnerability management solution, plays a crucial role in this domain. In this blog post, I’ll share my experience setting up a home lab to practice vulnerability management using Qualys.
Setting Up the Lab Environment
To begin with, We need to sign up for Qualys Community edition and then install Oracle VirtualBox to create a lab environment. I set up a Windows 10 virtual machine and installed the Qualys Virtual Scanner Appliance. For assessment, I deliberately used outdated software (Firefox 1.0.4, VLC Player 1.1.1) known for vulnerabilities.
Follow the steps below to set up:
- Download VirtualBox for your PC.
- Install VirtualBox (VB) and the Windows 10 ISO file. 2.1. While installing Windows host in VB, change the network adapter to Bridge Adapter.
- Go to the Qualys site and register with your student account for a free trial.
- Go to the Windows host that you installed on VirtualBox, and ping your main computer’s IP address (command: ipconfig - to find your host IP address in Windows, ifconfig - Linux).
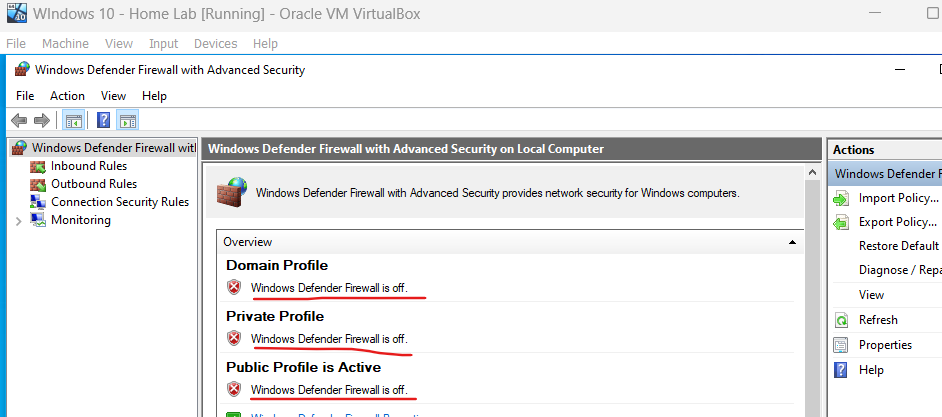
- Turn off firewalls if your Windows host won’t communicate with your main computer.
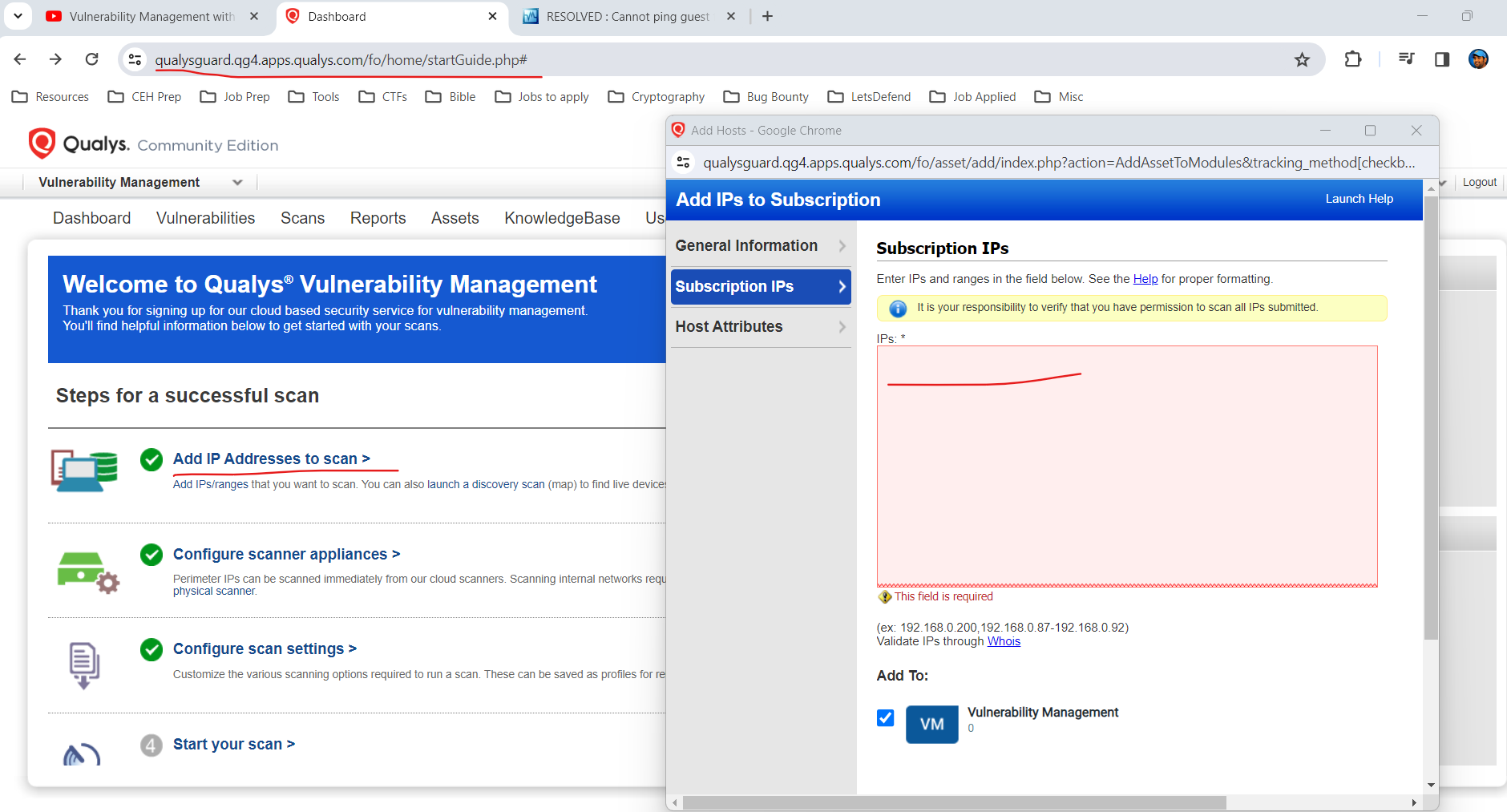
- Go to the Qualys dashboard and add IPs to scan, add your Windows host IP, which is in VirtualBox.
- Configure the scanner appliance (Add one if you don’t have) and set it up just like how you set up the Windows host.
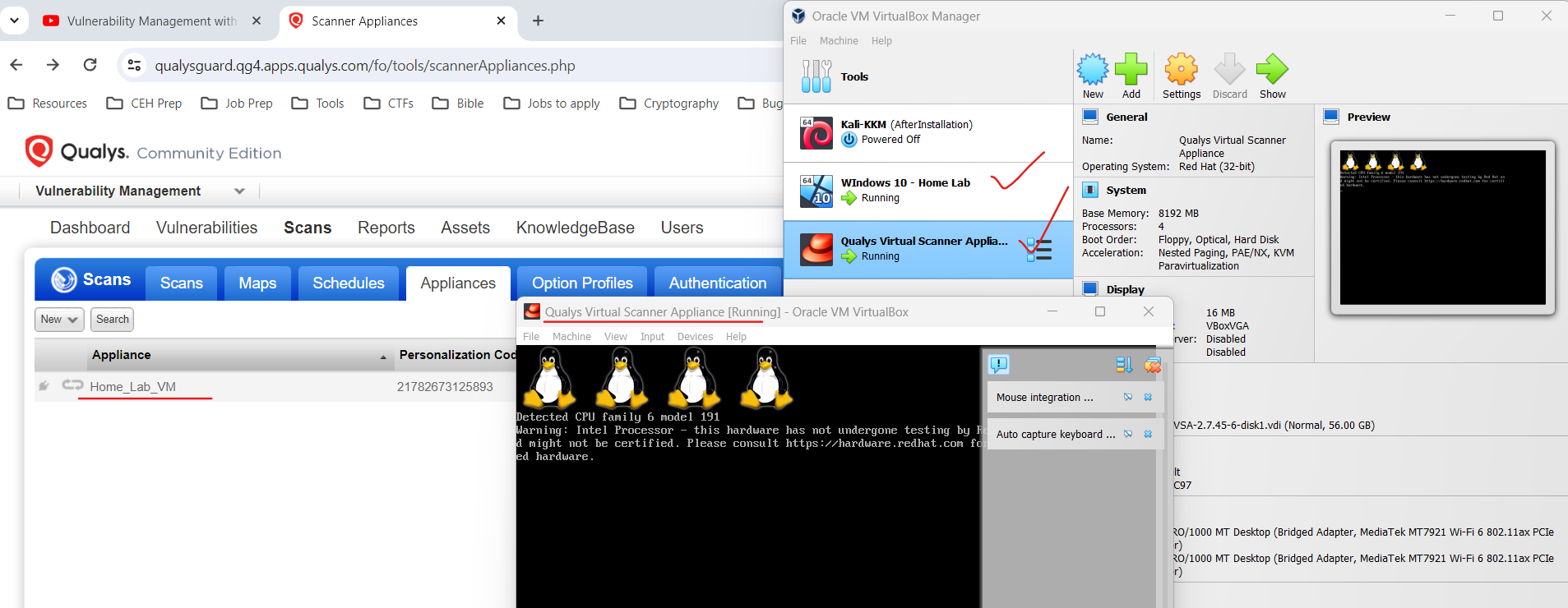
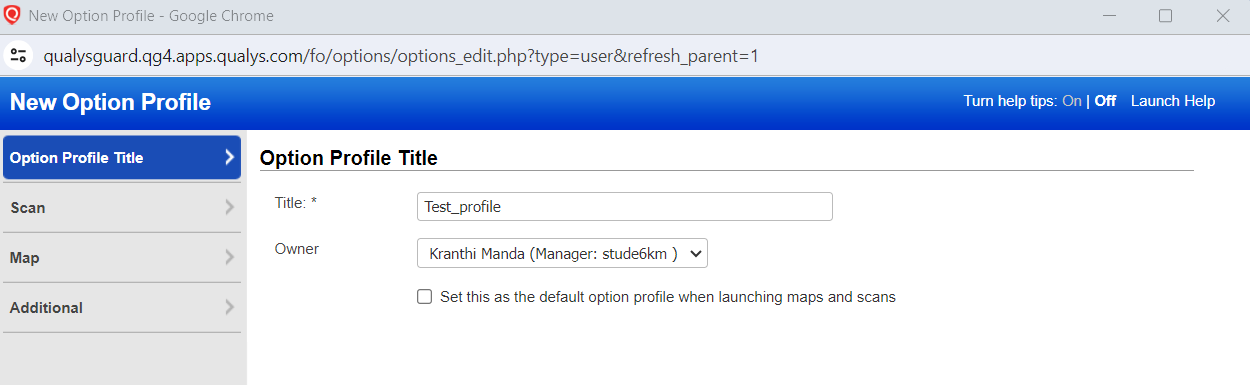
- Create a test profile under Scans -> New -> Option Profile.
- Now install a few softwares with outdated versions like VLC media player and Firefox.
Scanning: Credential and Non-Credential Scans
I performed both a non-credentialed scan and a credentialed scan on the virtual machine. The non-credentialed scan utilizes network based techniques exclusively to detect vulnerabilities, whereas credentialed scan involves granting Qualys the administrative access to the Windows host system, allowing for a more thorough vulnerability assessment. 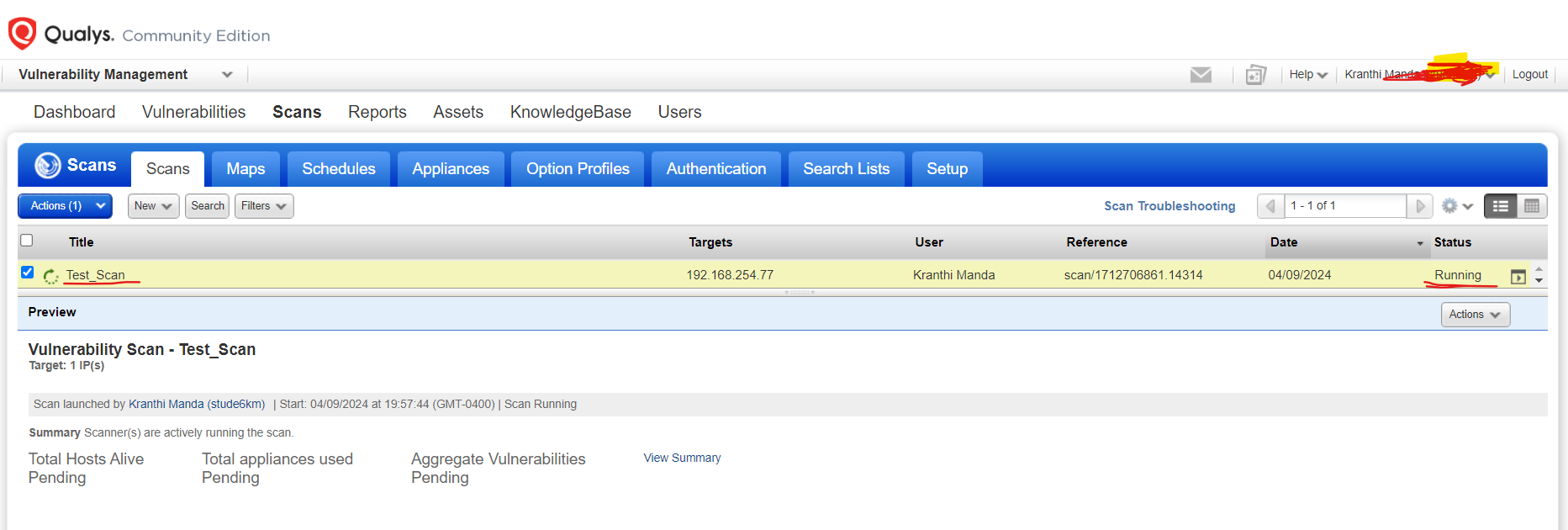
Scan results analysis
Go to completed scan and click on view, It will generate a detailed report. Upon completion of the scan, I carefully analyzed the scan results generated by Qualys, which outlined vulnerabilities detected within the Windows 10 host. The non-credentialed scan identified general network level vulnerabilities, and it categorized the VM’s risk level at 3.0/5.0
Unauthenticated scan
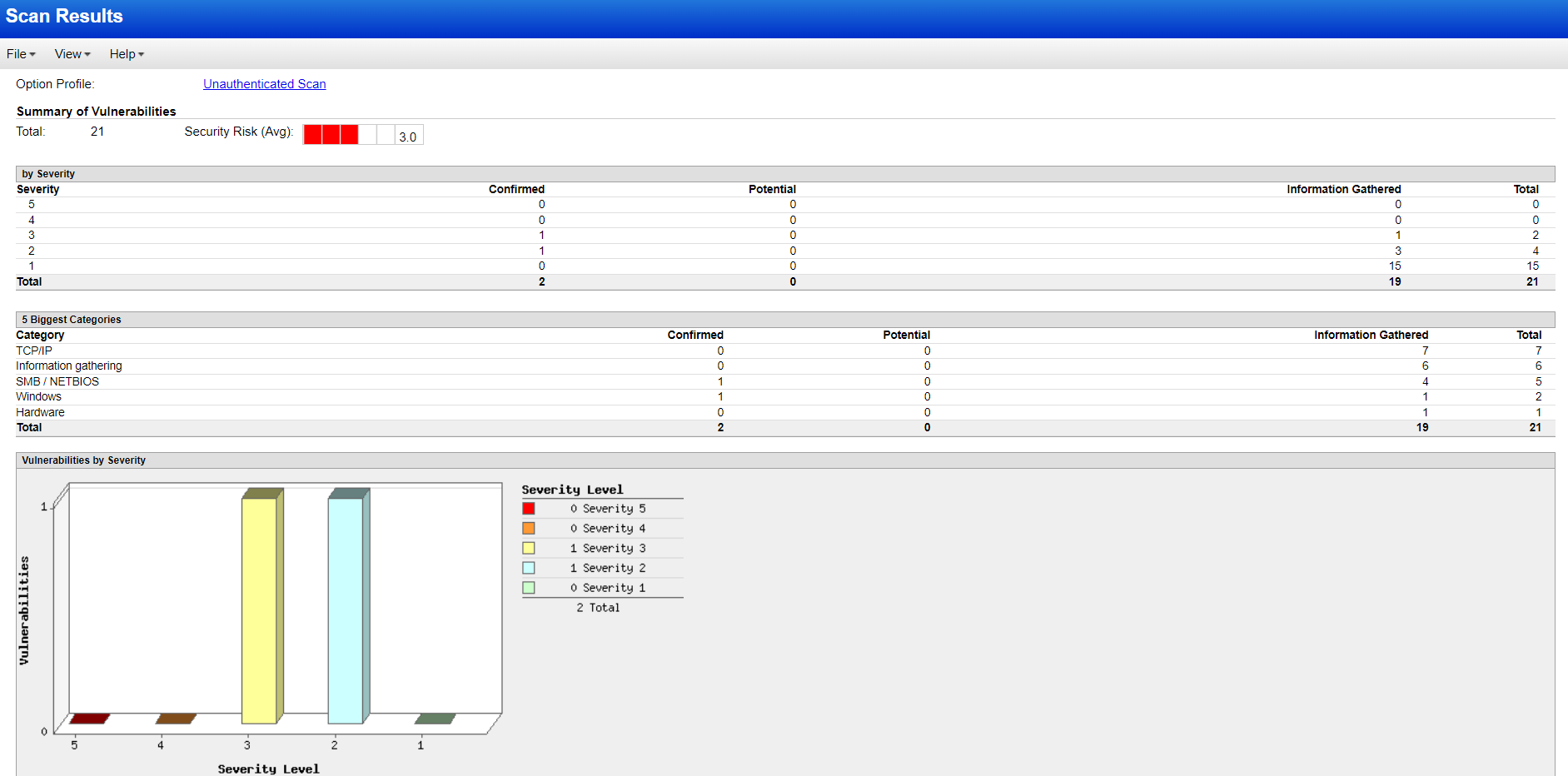 The good thing here is that we can see the solution and take immediate remediation actions based on the vulnerability. Even though I have installed vulnerable software, the unauthenticated scan didn’t find any of them. Did you observe that?
The good thing here is that we can see the solution and take immediate remediation actions based on the vulnerability. Even though I have installed vulnerable software, the unauthenticated scan didn’t find any of them. Did you observe that? 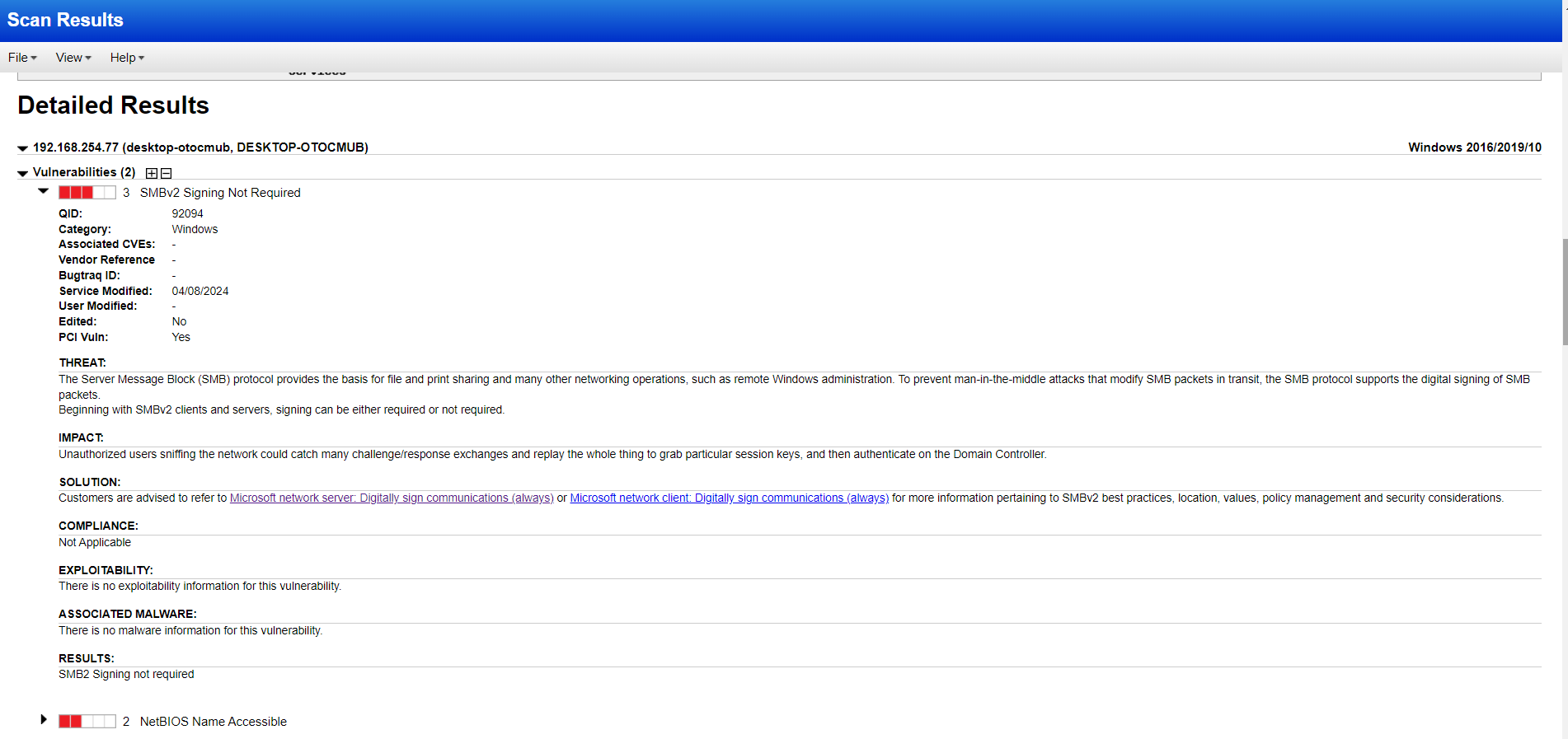
Authenticated scan
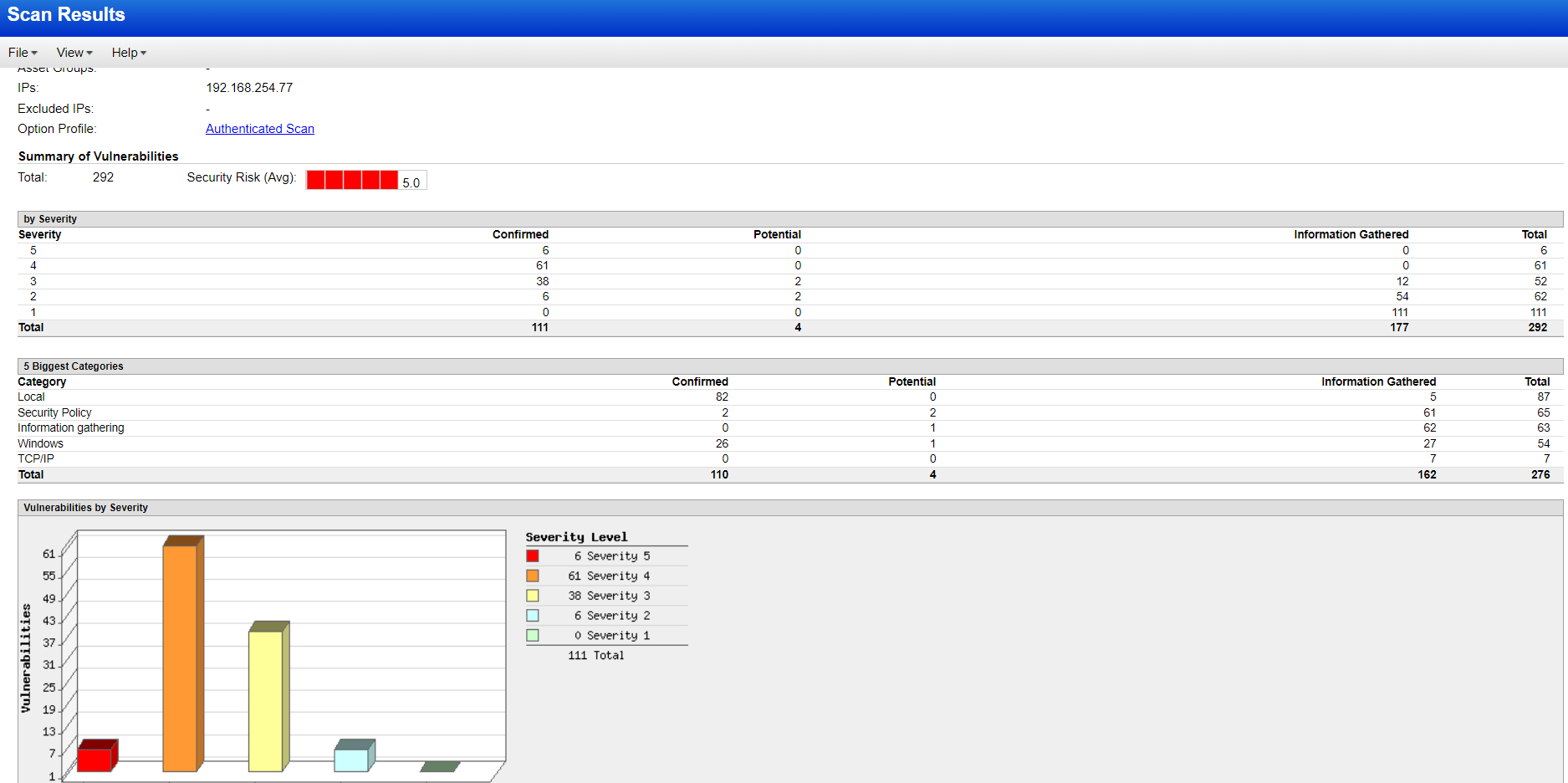 For this scan, I provided the admin credentials and initiated the scan. This time, it categorized the VM’s risk level as 5.0/5.0. Yeah, our host is at a high risk now. By uninstalling those vulnerable softwares, we can somehow mitigate the risk. Also, for every vulnerability, there is a solution tab that guides us on how to take action.
For this scan, I provided the admin credentials and initiated the scan. This time, it categorized the VM’s risk level as 5.0/5.0. Yeah, our host is at a high risk now. By uninstalling those vulnerable softwares, we can somehow mitigate the risk. Also, for every vulnerability, there is a solution tab that guides us on how to take action. 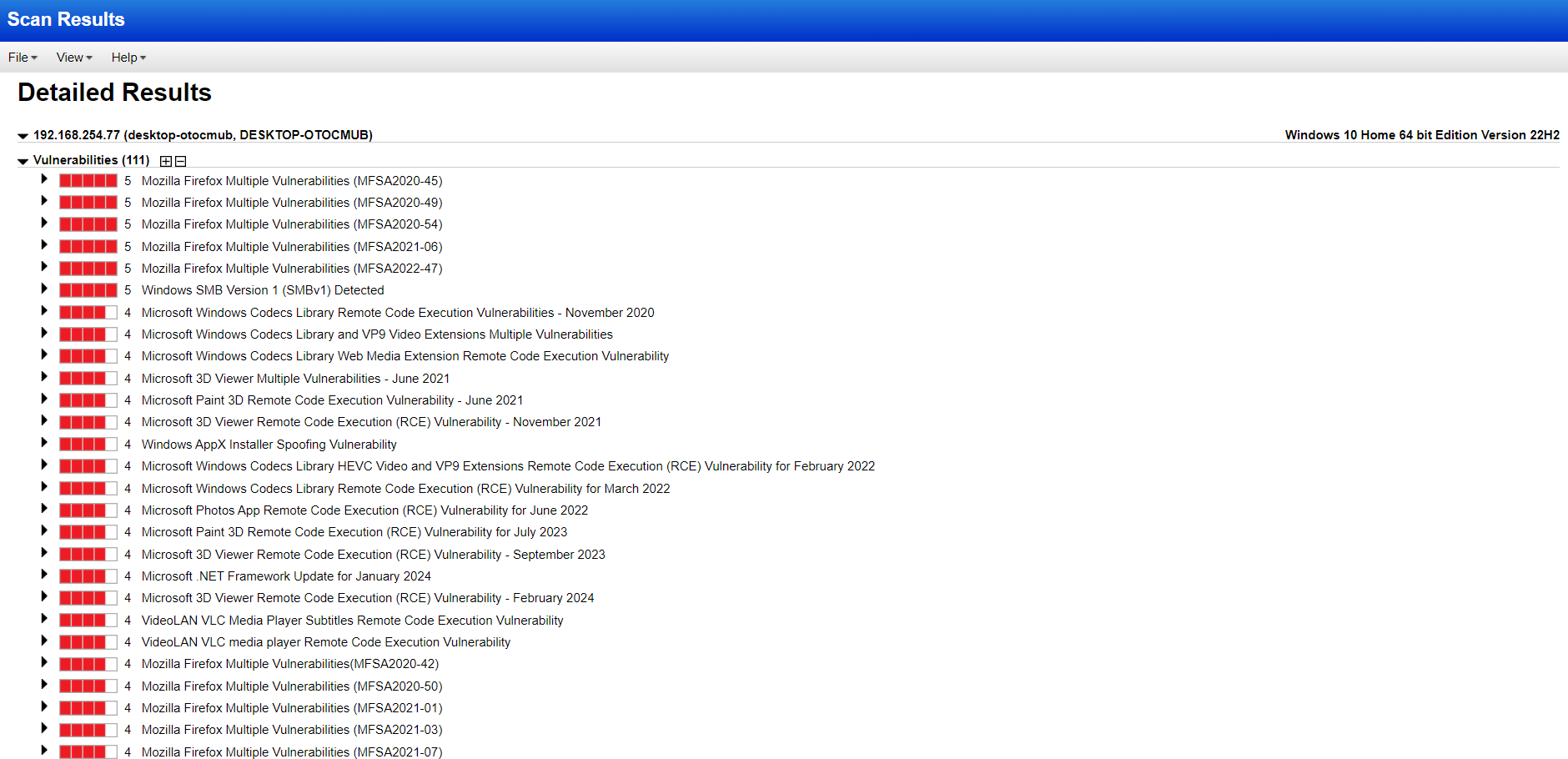
In the screenshot below, you can see detailed information about the vulnerability, like the associated CVEs (Common Vulnerabilities and Exposures) and QIDs (Qualys IDs), as well as how it can impact our system. 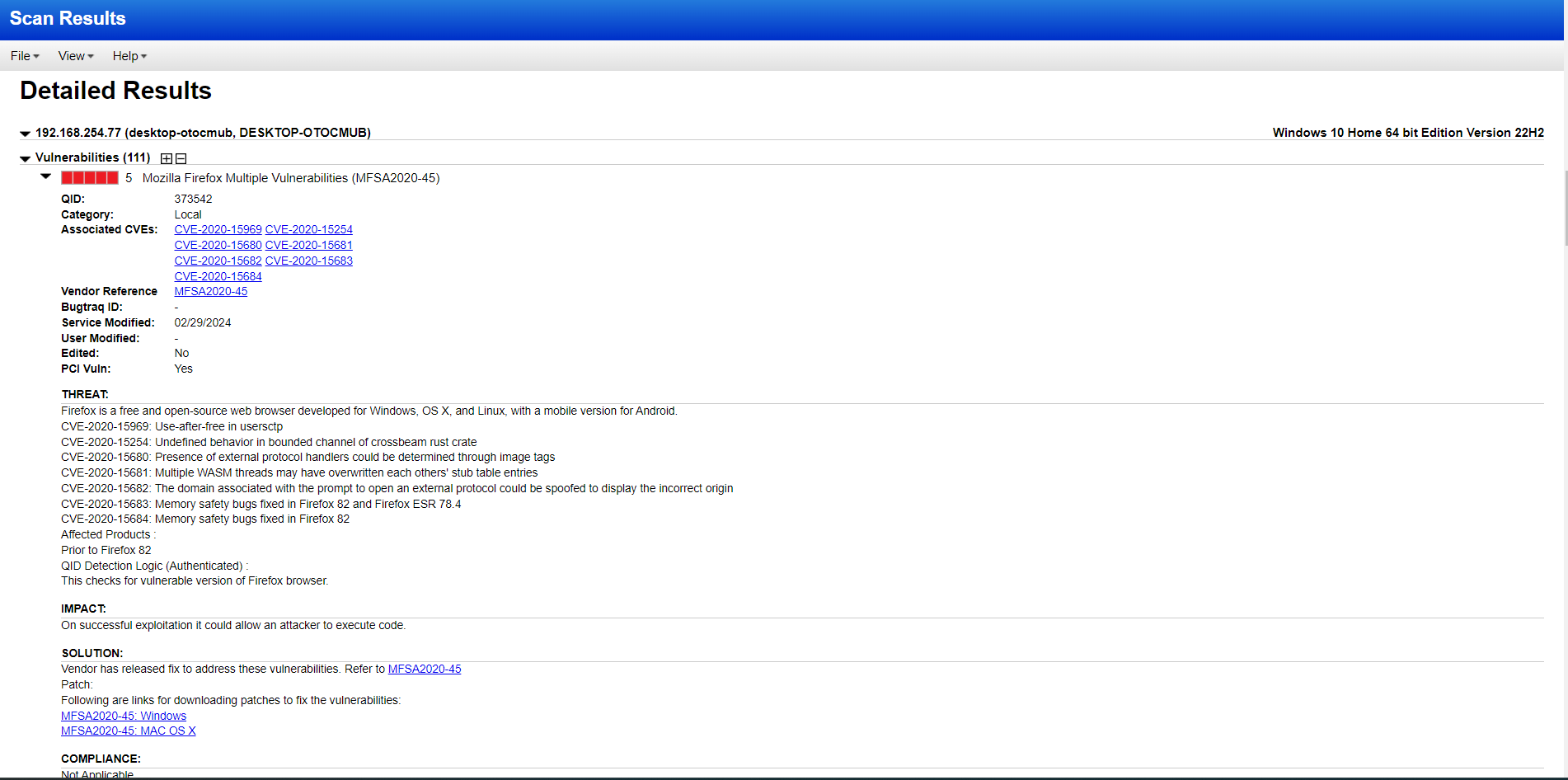
Remediation methods
With the vulnerability details I have in report, I started fixing the issues. I uninstalled outdated software, updated Firefox to the newest version, and enabled the firewall. I also researched the vulnerabilities listed in the scan report and addressed them accordingly by applying updates. These actions helped lower the vulnerability risk of the virtual machine. In a real work environment, I believe there are additional methods for remediation beyond what I’ve done here.
Conclusion
So with this project, I had the chance to explore into Qualys vulnerability management. I set up a lab, installed outdated software, and ran both credentialed and non-credentialed scans. After reviewing the scan results and implementing the recommendations, I fixed the vulnerabilities on the Windows 10 host. This hands-on experience showed me how effective Qualys can be in reducing security risks. 
Also, I completed a 5-hour Qualys course alongside this lab. That course covered a wide range of topics beyond the lab, including different scanning options, working with multiple hosts, installing cloud agents, and generating detailed vulnerability reports for individual hosts and many much more.